Adapting to Threats, Achieving HITRUST CSF Compliance with Audisocon's Support
As your comprehensive HITRUST partner, Audisocon provides a range of services, from readiness assessments to certification support, all from a reliable source.
We acknowledge that some organizations may already have internal teams or solutions, and only need support in specific areas. Therefore, we offer the flexibility to provide partial or specific support, tailored to your organization's specific needs. Our team will work closely with you to understand your requirements and provide customized services accordingly.
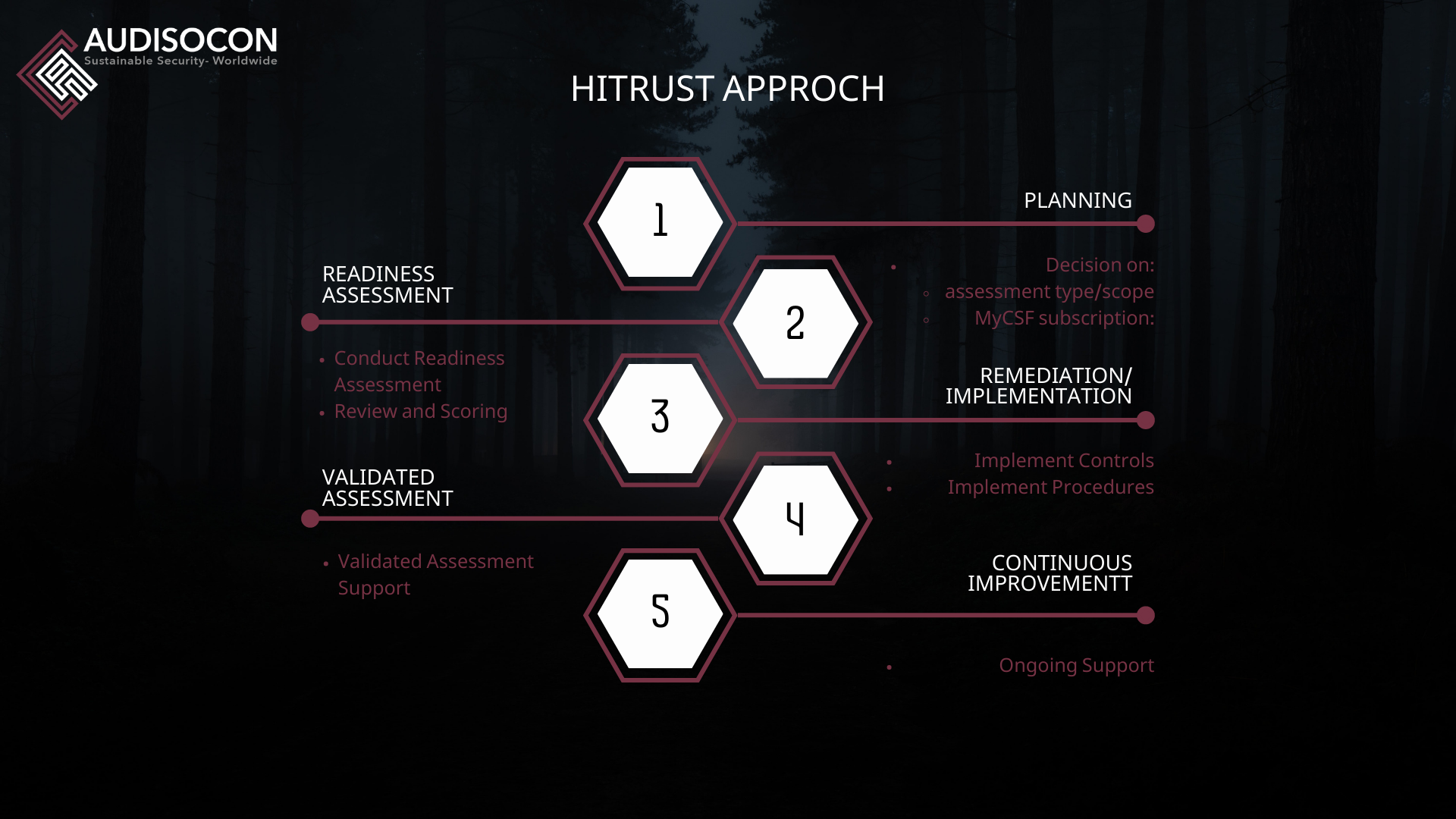
Elevate your organization's security standards with Audisocon's HITRUST approach.
Planning
- We support you in determining the right HITRUST assessment type.
HITRUST has updated its assessments in 2023, offering three distinct options to cater to the diverse needs of different companies. Choosing the right assessment type is crucial for ensuring cost-effectiveness, minimizing compliance department burden, and meeting customer requirements. e1 Assessment:
This is the entry-level assessment type and is designed for organizations that are just starting out on their HITRUST journey. It focuses on a limited set of controls and is designed to be cost-effective and relatively straightforward to implement.
i1 Assessment:
The intermediate-level assessment is designed for organizations that have a more mature HITRUST program in place or require a more comprehensive assessment. It covers a larger number of controls and provides a deeper level of scrutiny than the e1 assessment.
r2 Assessment:
The r2 Assessment is the most comprehensive of the three options. It is designed for organizations with the highest risk exposure.
The r2 Assessment allows organizations to tailor their security controls based on authoritative sources, regulatory requirements, system requirements and company specific needs. The r2 Assessment requires a significant level of effort, but the added assurance it provides makes it well worth the investment for organizations in highly regulated industries or those with a large attack surface.- Audisocon can assist your company in choosing the right MyCSF subscription for your HITRUST assessment needs.
Subscription Levels:
HITRUST offers various subscription levels for their MyCSF platform to meet the needs of different organizations. Report only access provides the basic functionality necessary to conduct an assessment and submit it for processing. On the other hand, an annual subscription to MyCSF offers advanced features to streamline the assessment process and better manage the organization's HITRUST CSF adoption. In essence, the subscription level you choose will determine the level of functionality and support available to you.
Readiness Assessment
- Audisocon conducts the Readiness Assessment together with your internal and external stakeholders.
The HITRUST Readiness Assessment:
The HITRUST rediness-assessment is an internal audit of an organization's preparedness for a validated HITRUST assessment. It is performed using the MyCSF online tool provided by HITRUST and includes features such as Corrective Action Plans, Custom Assessments, Evidence Support, and Comprehensive Reporting.
- Furthermore, we will Review and Score all security controls with regards to the HITRUST Maturity Model.
The HITRUST Maturity Model:
- The HITRUST Maturity Model evaluates an organization's compliance with the HITRUST CSF by assessing the level of each control in five different areas:
- Policies,
- Procedures,
- Implemented,
- Measured,
- and Managed.
- The evaluation criteria for each area includes the existence of formal and up-to-date policies and procedures, consistency of implementation, routine assessments and metrics, and effective corrective actions.
- Your company may not be required to evaluate all the requirements for every type of assessment. In the case of i1 and e1 assessments, only the "Implemented" level of the controls needs to be evaluated. However, for r2 assessments, the first three levels (Policies, Procedures, and Implemented) must be evaluated, and if desired, all five levels (Measured and Managed) can also be evaluated.
- Acquire the comprehensive HITRUST Readiness Assessment Report and a tailored Implementation Plan for each domain, providing a clear roadmap for successful HITRUST certification.
The HITRUST Readiness-Assessment Report:
The HITRUST readiness assessment report is a document issued by HITRUST that confirms the completion of the readiness assessment. It serves as evidence that the assessment has been carried out and provides a comprehensive evaluation of an organization's compliance. The report includes information about the scope (but your company can also get a report without the scope statement) and objectives of the assessment, the methodology used, and the results obtained. It also identifies areas of strength and areas for improvement and provides recommendations for addressing any gaps in compliance with HITRUST requirements. This report serves as an important resource for organizations to understand their current state of compliance with HITRUST and to plan the necessary steps to achieve HITRUST certification.
Remediation and Implementation
- After the HITRUST readiness assessment, organizations must complete remediation and implementation activities to achieve certification.
Remediation and Implementation Activities
Remediation involves fixing identified weaknesses and non-compliant areas, whereas implementation involves putting into practice the necessary controls and processes to meet HITRUST requirements. This process may involve updating policies and procedures, implementing new technologies, and providing employee training. The Implementation/Remediation Plan outlines the specific steps that need to be taken to address the identified gaps and achieve compliance with HITRUST requirements. The plan may be organized by domain, outlining the specific actions needed to address each area.
HITRUST Validated Assessment
- The HITRUST Validated Assessment is a crucial step towards achieving HITRUST certification.
HITRUST Validated Assessment:
It involves a thorough review of the organization HITRUST implementation by HITRUST Authorized External Assessors. These assessors perform the assessment and then submit their final report to HITRUST for quality assurance review. The purpose of this review is to determine whether the organization has met the minimum requirements for certification and the quality requirements set by HITRUST.
Audisocon cannot conduct a validated HITRUST assessment as we are not a validated external assessor. However, we can assist in finding suitable partners for the assessment and provide support with evidence collection and the audit process, as well as the actual assessment. We will also support the organization in coordinating with an external assessor to conduct the assessment, and assist with the submission to HITRUST for quality assurance review and the process of obtaining certification.
- Upon completion of the validated assessment, organizations will receive a comprehensive HITRUST Validated Assessment Report, providing them with a clear and thorough overview of their compliance status.
The HITRUST Validated Assessment Report:
The HITRUST Validated Assessment Report is a comprehensive document that provides a detailed overview of an organization's compliance with the HITRUST Common Security Framework (CSF). It includes the following sections:
- HITRUST Background: Information on the HITRUST Common Security Framework.
- HITRUST Background: Information on the HITRUST Common Security Framework.
- Letter of Certification: A letter that certifies the organization's compliance with HITRUST CSF.
- Representation Letter from Management: A letter from the organization's management that represents their commitment to HITRUST CSF compliance.
- Assessment Context: A description of the context in which the assessment was performed.
- Scope of the Assessment: Information on the scope of the assessment, including the areas that were assessed and the extent of the assessment.
- Procedures Performed by the External Assessor: A description of the procedures that were performed by the external assessor to evaluate the organization's compliance with HITRUST CSF.
- Assessment Results: Detailed results of the assessment, including the organization's compliance with HITRUST CSF controls and any identified gaps.
- PRISMA Control Maturity Model Overview: An overview of the PRISMA Control Maturity Model, which is used to assess the maturity of an organization's information security program.
- Controls by Assessment Domain: A summary of the assessment results by domain, including the results for each of the HITRUST CSF domains. The report also includes Appendices that provide additional information, such as Corrective Action Plans, Additional Gaps Identified, and Assessment Results. The report serves as a valuable resource for organizations to understand their compliance with HITRUST CSF and to identify areas for improvement.
Ongoing support:
- Organizations must maintain and regularly renew their HITRUST certification. This requires continuous improvement of their security controls to ensure they remain compliant with HITRUST requirements. To support this effort, Audiocon offers ongoing support for HITRUST certification maintenance and recertification.
Audisocon offers a full suite of HITRUST support services, guiding you the way to ensure your organization reaches its cybersecurity objectives. Choose us for a stress-free and efficient HITRUST journey.
Get in touch with us to schedule a consultation.
